APT
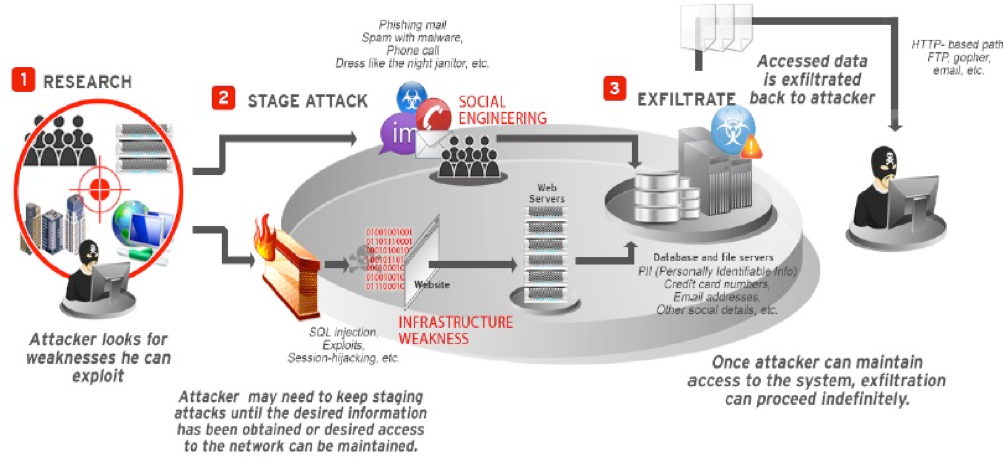
Advanced persistent threat (APT) hackers and malware are more prevalent and sophisticated than ever. APTs are professional hackers, working either for their government or relevant industries, whose full-time job is to hack specific companies and targets. They perform actions relevant to their sponsor’s interests, which can include accessing confidential information, planting destructive code, or placing hidden backdoor programs that allow them to sneak back into the target network or computer at-will.
APT hackers are very skilled and have the huge operational advantage in that they will never be arrested. Imagine how much more successful and persistent any other thief might be if they could get the same guarantee.
Still, they don’t want their activities to be immediately noticed by their targets, because it would complicate their mission. A successful APT breaks into networks and computers, gets what they need, and slips out unnoticed. They prefer to be “slow and low.” They don’t want to generate a lot of strange-looking auditable events, error messages, or traffic congestion, or to cause service disruptions.
Most APTs use custom code to do their activities, but prefer, at least at first, to use publicly known vulnerabilities to do their dirty work. That way, if their activities are noticed, it’s harder for the victim to realize that it’s an APT versus the regular, less serious, hacker or malware program.
With that said, how can you recognize something that’s meant to be silent and unnoticed?
Recognizing an APT
Because APT hackers use different techniques from ordinary hackers, they leave behind different signs. Over the past two decades the following five signs are most likely to indicate that your company has been compromised by an APT. Each could be part of legitimate actions within the business, but their unexpected nature or the volume of activity may bear witness to an APT exploit.
- Increase in elevated log-ons late at night
APTs rapidly escalate from compromising a single computer to taking over multiple computers or the whole environment in just a few hours. They do this by reading an authentication database, stealing credentials, and reusing them. They learn which user (or service) accounts have elevated privileges and permissions, then go through those accounts to compromise assets within the environment. Often, a high volume of elevated log-ons occur at night because the attackers live on the other side of the world. If you suddenly notice a high volume of elevated log-ons across multiple servers or high-value individual computers while the legitimate work crew is at home, start to worry.
- Widespread backdoor Trojans
APT hackers often install backdoor Trojan programs on compromised computers within the exploited environment. They do this to ensure they can always get back in, even if the captured log-on credentials are changed when the victim gets a clue. Another related trait: Once discovered, APT hackers don’t go away like normal attackers. Why should they? They own computers in your environment, and you aren’t likely to see them in a court of law.
These days, Trojans deployed through social engineering provide the avenue through which most companies are exploited. They are fairly common in every environment, and they proliferate in APT attacks.
- Unexpected information flows
Look for large, unexpected flows of data from internal origination points to other internal computers or to external computers. It could be server to server, server to client, or network to network.
Those data flows might also be limited, but targeted — such as someone picking up email from a foreign country. I wish every email client had the ability to show where the latest user logged in to pick up email and where the last message was accessed. Gmail and some other cloud email systems already offer this.
This has become harder to perform because so much of today’s information flows are protected by VPNs, usually including TLS over HTTP (HTTPS). Although this used to be rare, many companies now block or intercept all previously undefined and unapproved HTTPS traffic using a security inspection device chokepoint. The device “unwraps” the HTTPS traffic by substituting its own TLS digital and acts as a proxy pretending to be the other side of the communication’s transaction to both the source and destination target. It unwraps and inspects the traffic, and then re-encrypts the data before sending it onto the original communicating targets. If you’re not doing something like this, you’re going to miss the exfiltrated data leak.
Of course, to detect a possible APT, you have to understand what your data flows look like before your environment is compromised. Start now and learn your baselines.
- Unexpected data bundles
APTs often aggregate stolen data to internal collection points before moving it outside. Look for large (gigabytes, not megabytes) chunks of data appearing in places where that data should not be, especially if compressed in archive formats not normally used by your company.
- Focused spear-phishing campaigns
If I had to think of one of the best indicators, it would be focused spear-phishing email campaigns against a company’s employees using document files (e.g., Adobe Acrobat PDFs, Microsoft Office Word, Microsoft Office Excel XLS, or Microsoft Office PowerPoint PPTs) containing executable code or malicious URL links. This is the original causative agent in the vast majority of APT attacks.
The most important sign is that the attacker’s phish email is not sent to everyone in the company, but instead to a more selective target of high-value individuals (e.g., CEO, CFO, CISO, project leaders, or technology leaders) within the company, often using information that could only have been learned by intruders that had already previously compromised other team members.
The emails might be fake, but they contain keywords referring to real internal, currently ongoing projects and subjects. Instead of some generic, “Hey, read this!” phishing subject, they contain something very relevant to your ongoing project and come from another team member on the project. If you’ve ever seen one of these very specific, targeted phishing emails, you’ll usually end up shuddering a bit because you’ll question yourself about whether you could have avoided it. They are usually that good.
APT action plan
The question, then, is WHAT TO DO IF YOUR ORGANIZATION IS HIT BY AN APT ATTACK ? Every case is different and depends upon the details of the exploit. But in general, the cleanup and defense techniques are the very same ones we security IT admins have been taught and preached for the past 20 years. However, the problems and neglect we’ve been living with are finally catching up with us.
If there’s any silver lining to your organization being hit by an APT attack, it’s that the purse strings will probably starting loosening; at least you’ll have the money to spend to clean up the mess and institute that real security you’ve been talking about for the past five years or more. But money is only one part of the solution.
In a large environment, fixing everything at once is difficult. The best general approach is to identity your company’s data crown jewels and to protecting that part of the network as the highest priority. From there, move out to less risky assets.
Given that every APT attack varies, there’s no single defense plan. Still, the following steps could provide a useful start.
- Begin by threat modeling the past attacks against the biggest weaknesses in the environment. Doing so will help you identify where to begin defending and cleaning up.
- Implement least privilege authentication and access control. Don’t give users access to any resource they don’t use. This will help slow down damage from the next APT attack. Some of us at Microsoft (my full-time employer) are going so far as to tell people not to give anyone domain admin rights. Instead, use delegation.
- Harden computers following the vendor’s recommended security settings.
- Make sure you’re patching everything, especially popular browser add-ons.
- Implement application control whitelisting to stop new malicious programs from spreading around the environment.
- Implement strong password policies, with 12-character or longer complex passwords for standard user accounts. Elevated accounts should be even longer. Use two-factor authentication if long passwords are a problem or aren’t secure enough.
- Implement an enterprisewide log management system, with comprehensive alerting and auditing.
- Isolate secuirty domains and If computers shouldn’t talk to each other, don’t let them.
- Deploy an anomaly-detection product, such as HIDS (host-based intrusion detection systems) or NIDS (network-based intrusion detection systems).
- Make sure antivirus scanners check for updates every 24 hours or less and that they scan for hacking tools.
- Educate end user about the biggest risks, such as Adobe Acrobat and Java exploits, fake antivirus warnings, phishing sites, and so on.
There’s much more to battling an APT attack, but the list above should provide a good start. If your company hasn’t been hit by an APT, make sure it doesn’t join that organizations that will be reporting that they’re been compromised in a few months. If you’ve been hit by APT, I feel for you. Some of the ideas above should help.